
Decentralised AI for Situational Awareness
Thomas Kelly

Thomas Kelly
Olaf Lipinki

Jennifer Barnes-Nunn

John Birkbeck

Kryspin Varys

Radar Imaging for Non-Invasive for Brain Imaging and Anamoly Detection

Intelligent Coordination and Planning for Human-Robot Swarms
Sample-Efficient Exploration in Visually Complex Reinforcement Learning Tasks

Multi-modal event classification of social media content where training data is limited and/or emerging
Christopher Subia-Waud

Hsuan-Yang Wang

Kian Spencer
Epifanios Baikas

Konstantinos Drylerakis

Shannon How
Creating Augmented Reality Soundscape Experiences on Edge Devices
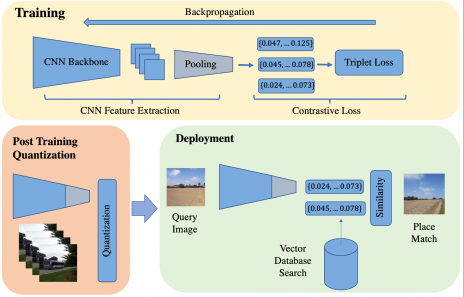
Efficient Visual Place Recognition for Real-Time Visual Perception

Sulaiman Sadiq

Jack Williamson
Matthew Pugh